Keptn API
In this section, the functionality and commands of the Keptn REST API are described.
Prerequisites
To access the Keptn API, a running Keptn installation is needed. If you have not set up Keptn yet, please start here.
To get the API token for authenticating API calls, please see here.
Access the Keptn API
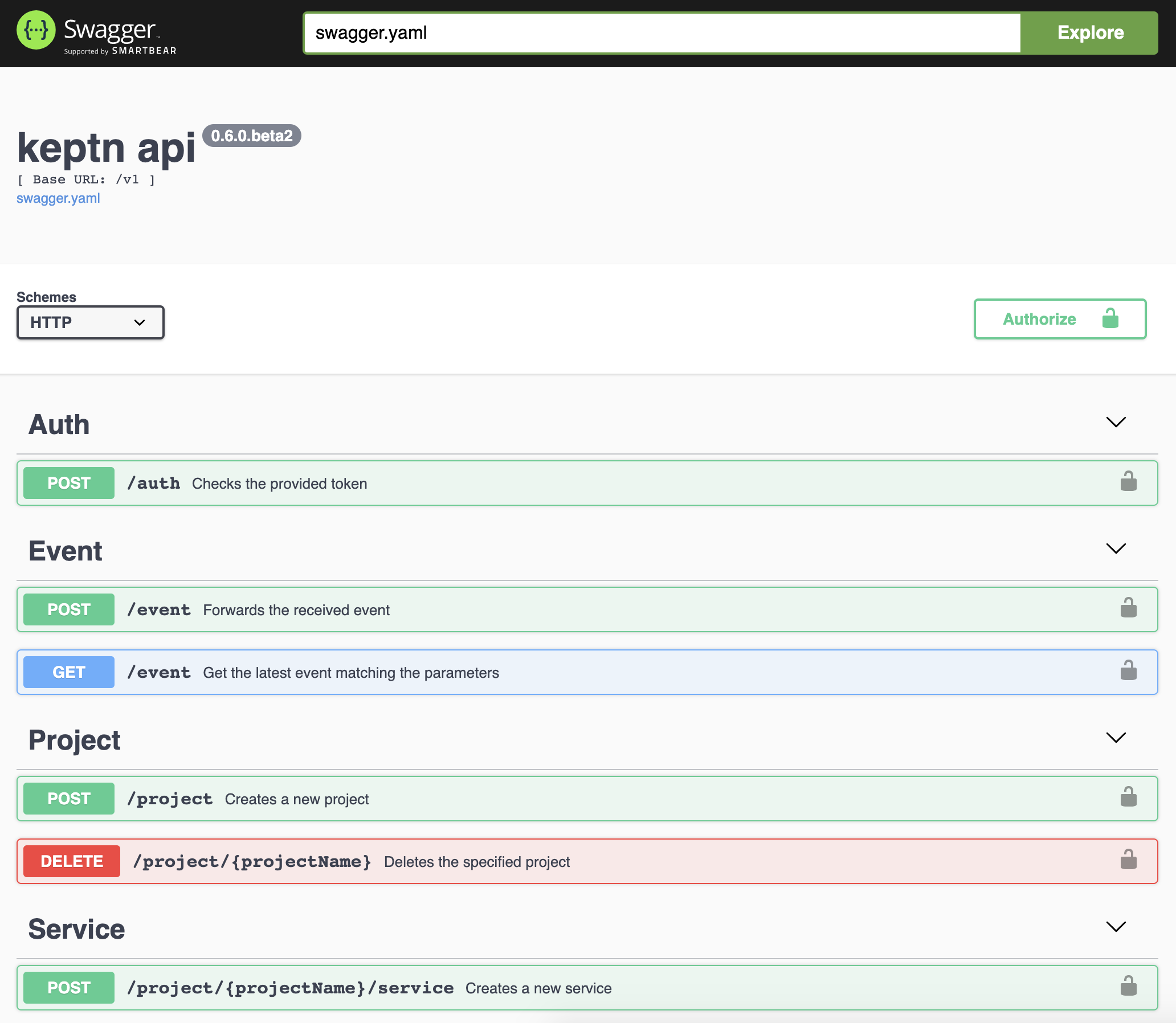
The Keptn API is documented in terms of a Swagger API documentation.
- Use the Keptn CLI to retrieve the endpoint of your Keptn API via the command
keptn status:
keptn status
Starting to authenticate
Successfully authenticated
CLI is authenticated against the Keptn cluster https://api.keptn.YOUR.DOMAIN
Access the Keptn Swagger API documentation in your browser at: https://api.keptn.YOUR.DOMAIN/swagger-ui/
The index page of the Swagger API documentation looks as follows:
Explore the Keptn API
Select one of the two API collections:
api-servicecontains endpoints to create/delete a project, to create service, and to send/get events.configuration-serviceprovides GET endpoints for project/stage/service and endpoints for resource management.
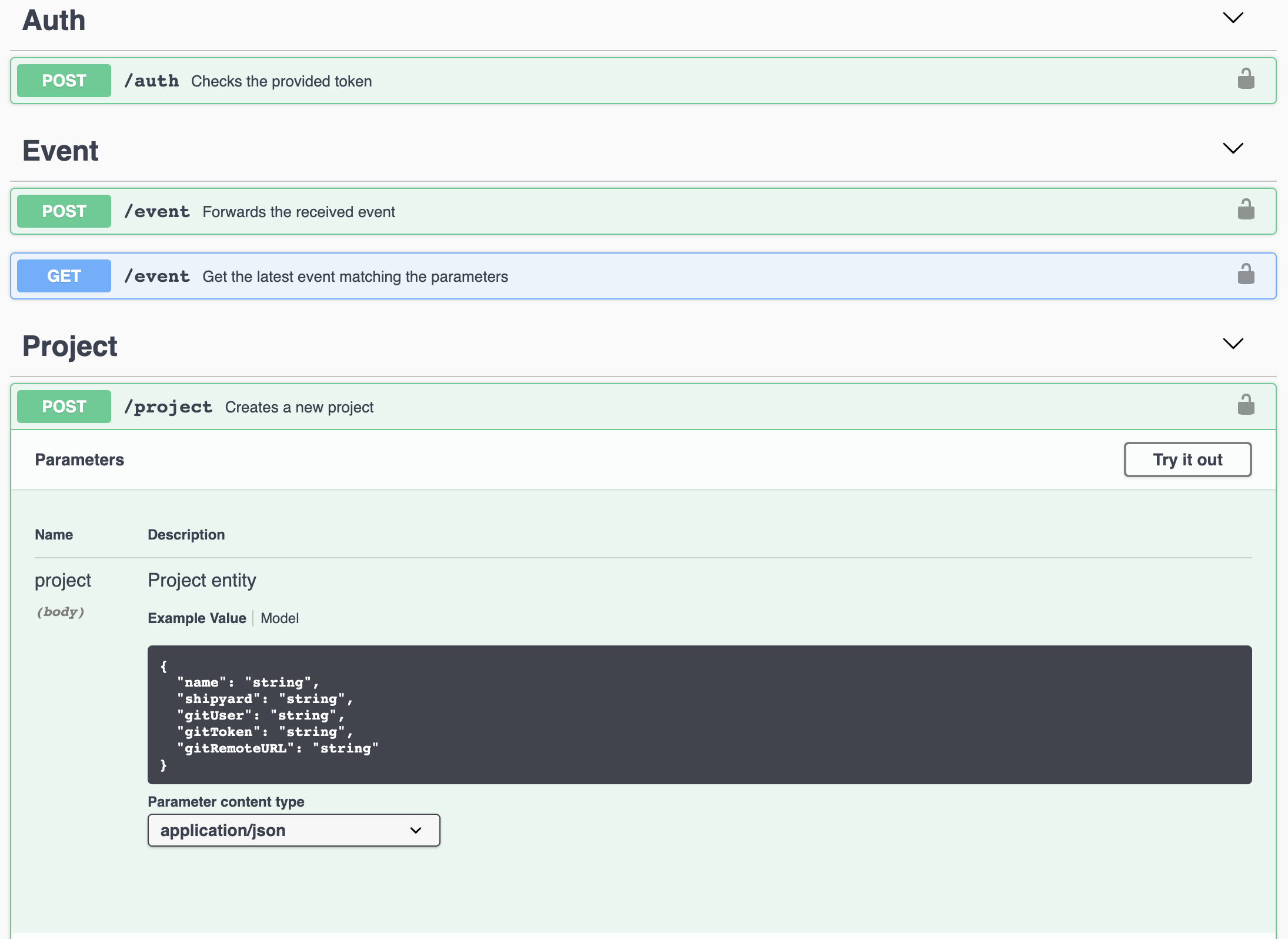
- Clicking on an endpoint reveals more details how to use it, including definitions and examples of the payload.
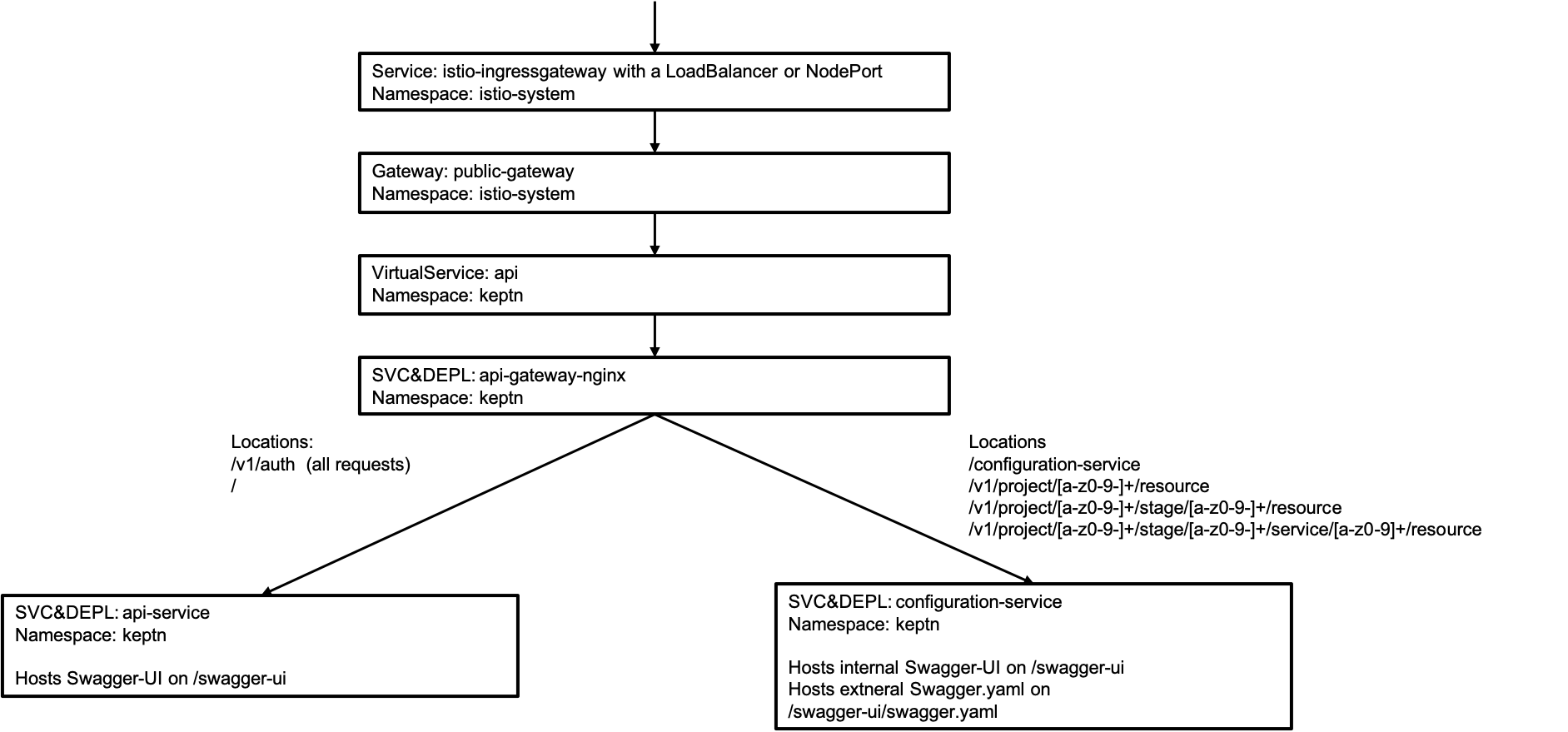
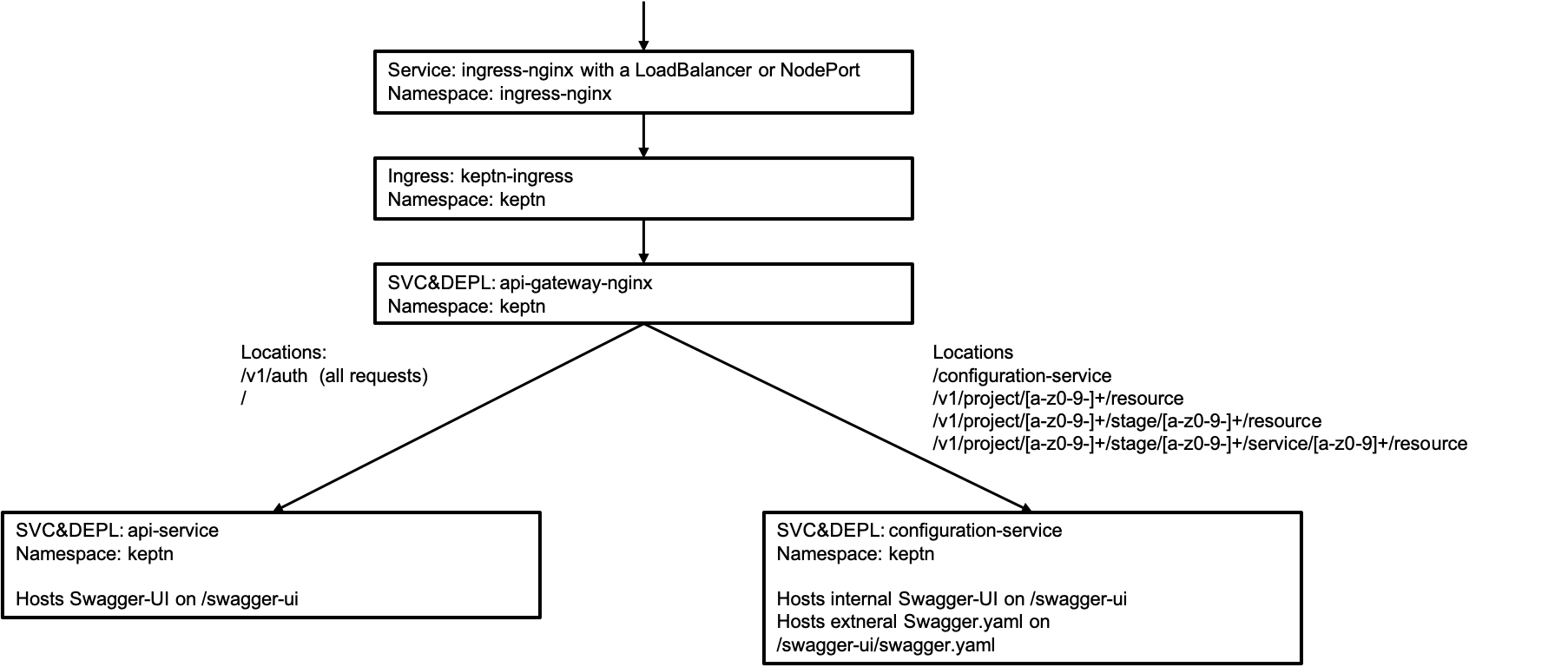
Architecture Details of Keptn API
- Keptn 0.6.2 introduced an NGINX as new K8s deployment and service. This NGINX allows to route the traffic and ensures that all requests are authenticated using the
/authendpoint of theapi-service. - The
api-servicenow does not implement endpoints of theconfiguration-serviceanymore. - The
configuration-serviceis exposed to the public. Endpoints that are not intended to be used from the public (e.g., deleting a project) are marked and the description is accordingly adapted.
Architecture for the full installation:
Architecture for the quality gates installation:
Technical Details of Cluster Gateway
The following descriptions are only valid for a full Keptn installation (i.e., a Keptn installation which was not installed for the quality-gates use case).
Keptn uses Istio for connecting and controlling the traffic.
In order to receive incoming and outgoing connections,
a Gateway named public-gateway is available in the istio-system namespace.
Details of the Gateway
apiVersion: networking.istio.io/v1alpha3
kind: Gateway
metadata:
name: public-gateway
namespace: istio-system
spec:
selector:
istio: ingressgateway
servers:
- port:
name: http
number: 80
protocol: HTTP
hosts:
- '*'
- hosts:
- '*'
port:
name: https
number: 443
protocol: HTTPS
tls:
mode: SIMPLE
privateKey: /etc/istio/ingressgateway-certs/tls.key
serverCertificate: /etc/istio/ingressgateway-certs/tls.crt
This Gateway accepts HTTP and HTTPS traffic. For the HTTPS traffic, Keptn generates a self-signed certificate during the installation.
If you already have a valid certificate for your domain and want to use this, please first configure your domain and, afterwards, manually update the used certificate in the Gateway. For adding a custom certificate, the Knative Documentation provides useful instructions.